Configure Elastic Load Balancing with SSL and AWS Certificate Manager for Bitnami Applications on AWS
Introduction
Load balancing is a technique commonly used by high-traffic Web sites and Web applications to share traffic across multiple hosts, thereby ensuring quick response times and rapid adaptation to traffic peaks and troughs. The Elastic Load Balancing service from Amazon Web Services (AWS) with Secure Sockets Layer (SSL) support makes it easy to add secure load balancing for Bitnami applications running on AWS.
This guide walks you through the process of configuring and testing an Elastic Load Balancer with an SSL certificate for a Bitnami application running on AWS.
Assumptions and prerequisites
This guide assumes that:
- You have a Bitnami application running on AWS, deployed using the AWS Marketplace or the AWS Console.
- You have the necessary credentials to log in to the Bitnami application instance.
- You own a domain name.
NOTE: This guide only covers the process of configuring a load balancer with an SSL certificate for a single Bitnami application. If you wish to balance load across multiple applications, additional steps will be required.
Step 1: Identify your Bitnami application instance in the AWS EC2 Console
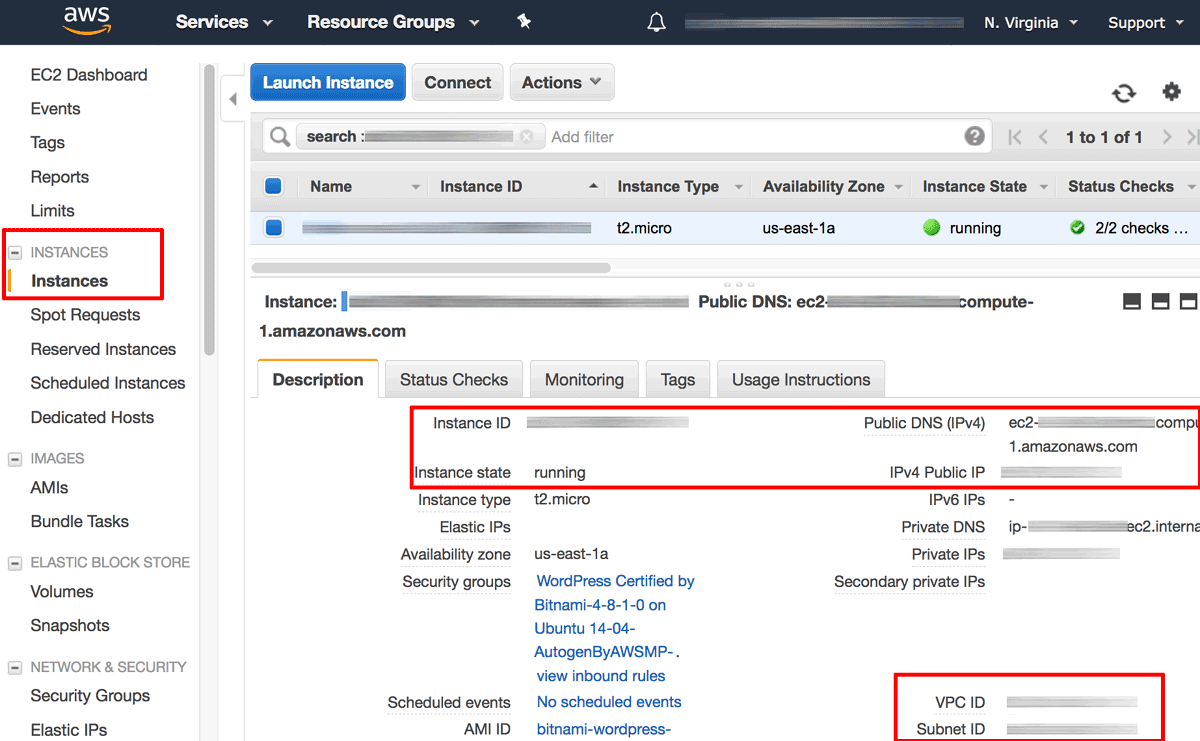
The first step is to identify your Bitnami application instance and collect various important bits of information, such as the instance ID, DNS name, public IP address, availability zone and Virtual Private Cloud (VPC) ID. To do this:
- Log in to the AWS EC2 console.
- From the “Services” menu, select the “EC2” service.
- From the EC2 Dashboard, select the “Instances -> Instances” menu item.
- Search for and select your Bitnami application instance from the list of available instances.
- From the instance details pane, note the instance ID, DNS name, public IP address, availability zone and VPC ID. You will need these details in subsequent steps.
- Browse to the instance’s public IP address and confirm that you get a positive response, such as the welcome page of the Bitnami application. This response will be necessary to pass health checks performed by the load balancer.
Step 2: Create an Elastic Load Balancer with HTTP and HTTPS support
Next, create an Elastic Load Balancer as follows:
-
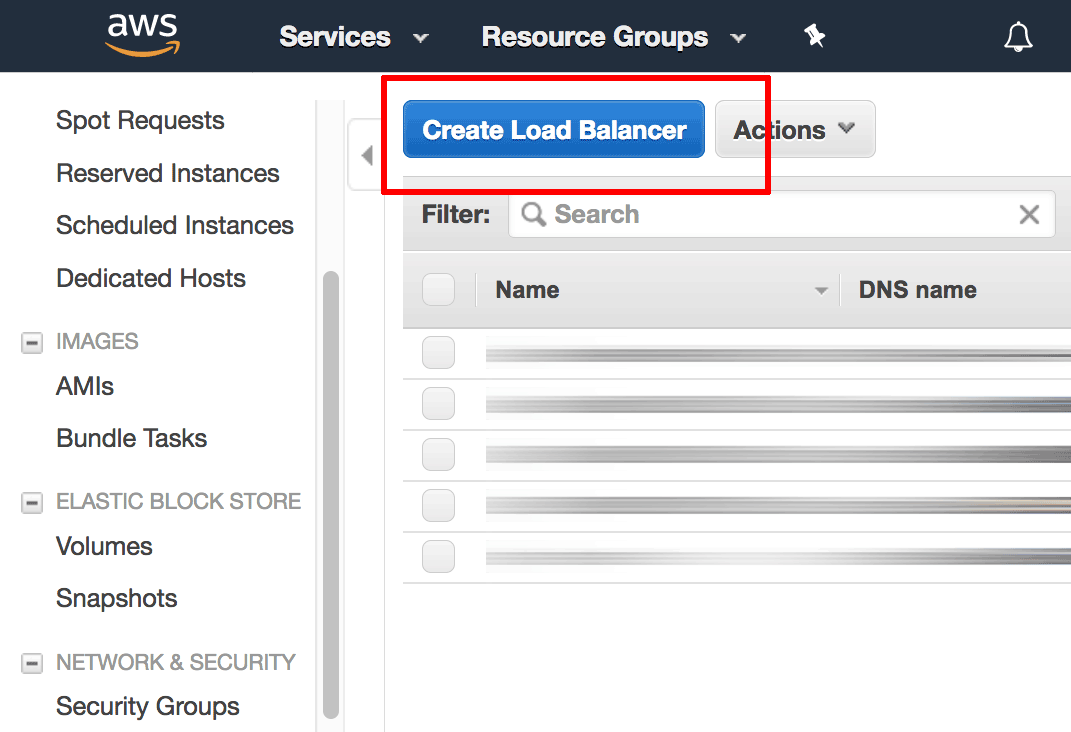
From the EC2 Dashboard, select the “Load Balancing -> Load Balancers” menu item.
-
Click the “Create Load Balancer” button.
-
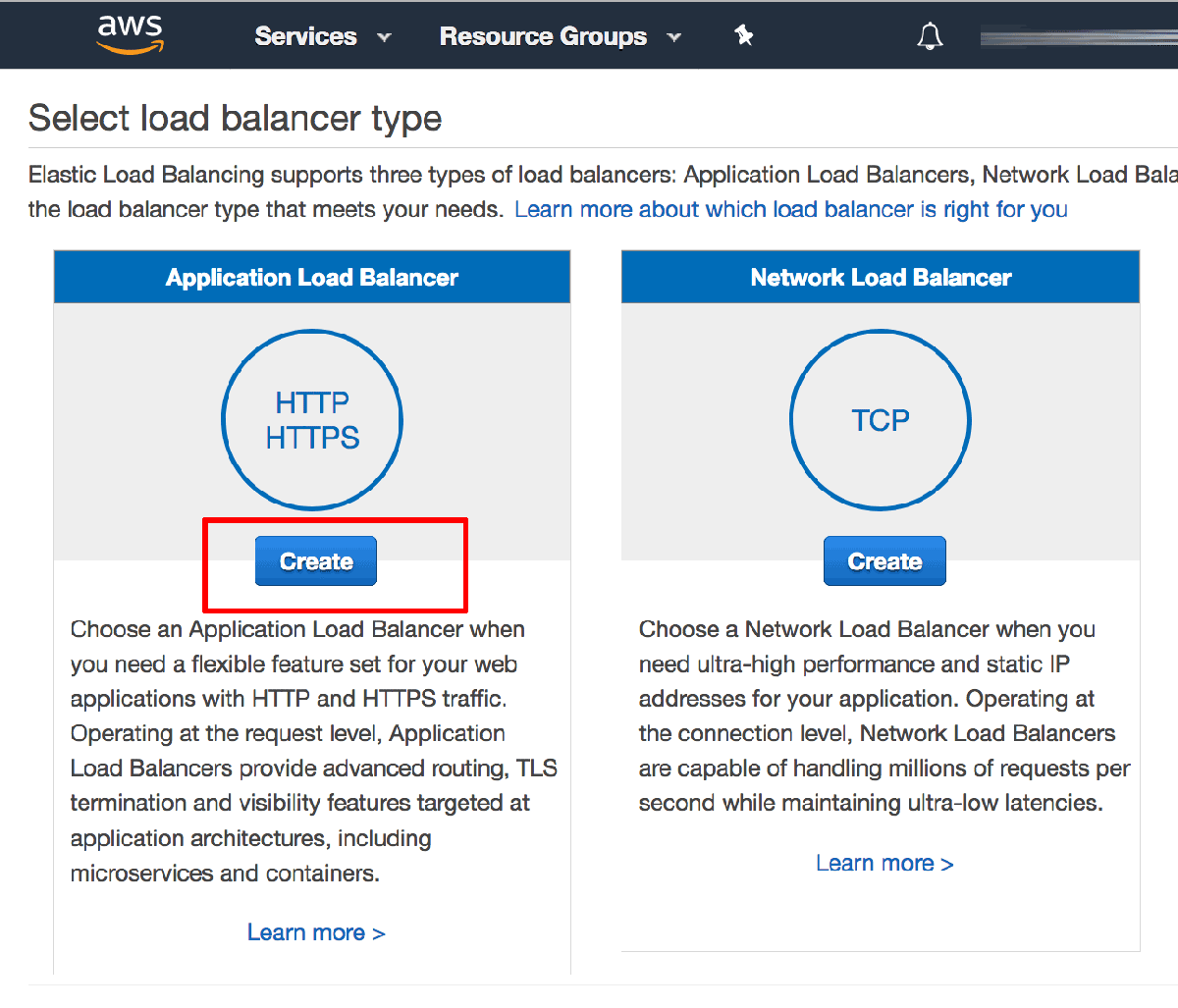
On the “Select Load Balancer type” page, select the “Application Load Balancer” option and click “Create”.
-
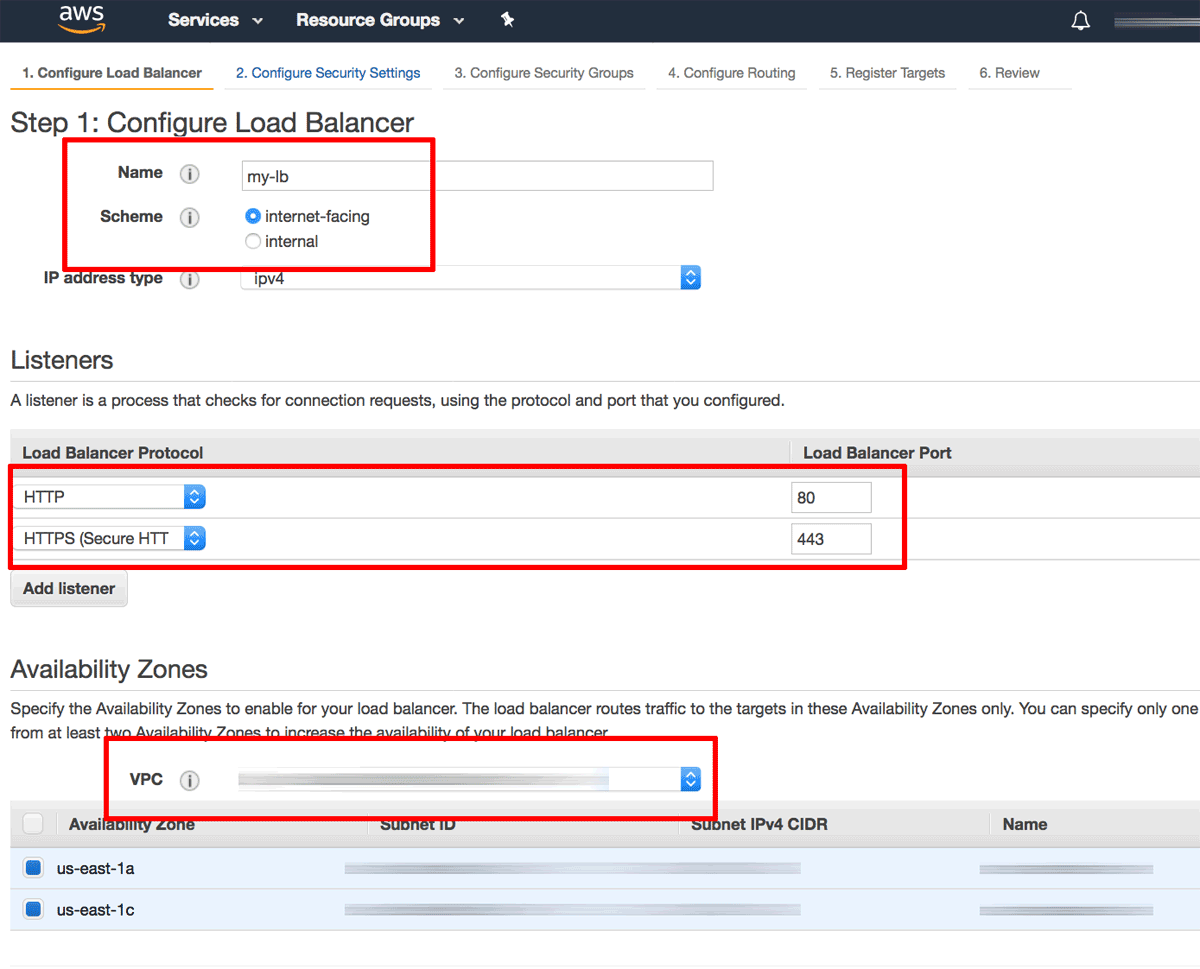
On the subsequent “Configure Load Balancer” page:
-
Enter a name for the load balancer and specify the scheme as “Internet facing”.
-
In the “Listeners” section, ensure that there is an HTTP listener on load balancer port 80. Click the “Add listener” button and add a second HTTPS listener on load balancer port 443. This configures the load balancer to handle both HTTP and HTTPS requests from clients.
-
In the “Availability Zones” section, select the same VPC as the one used by your Bitnami application instance and select a subnet from each availability zone.
-
Click the “Next: Configure Security Settings” button to proceed.
-
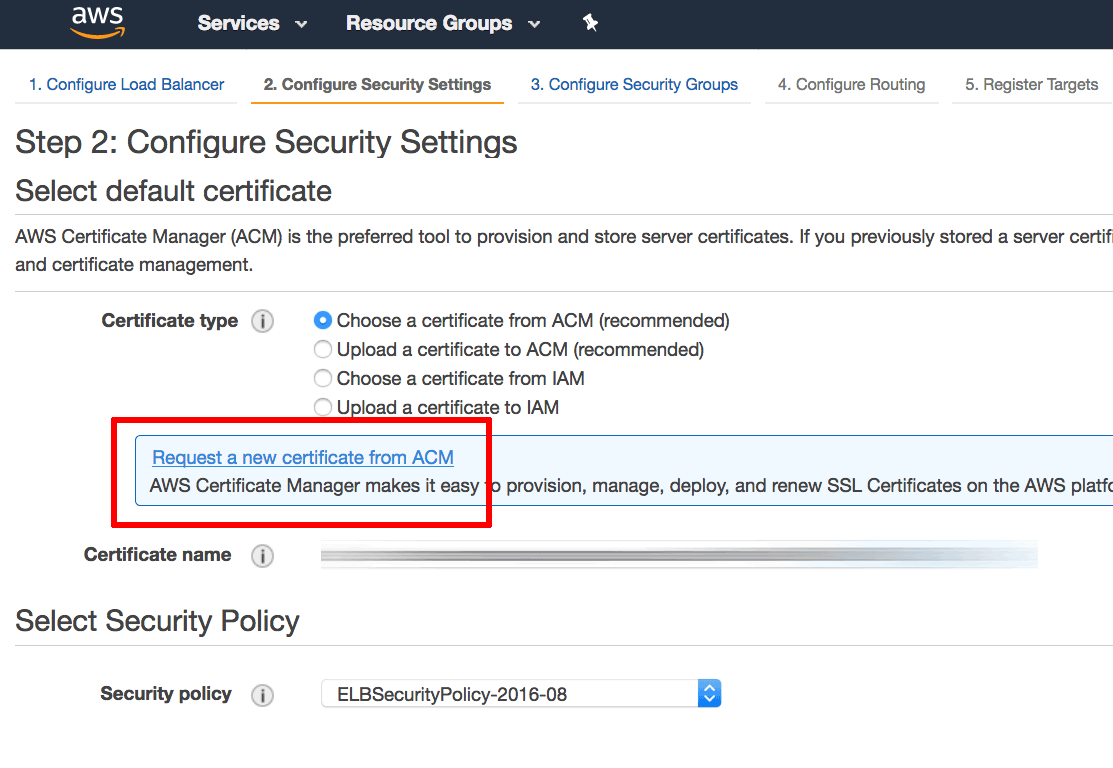
-
On the “Configure Security Settings” page, select the “Request a new certificate from ACM” option to create a new SSL certificate for your load balancer. This will launch the AWS Certificate Manager (ACM) in a new window.
-
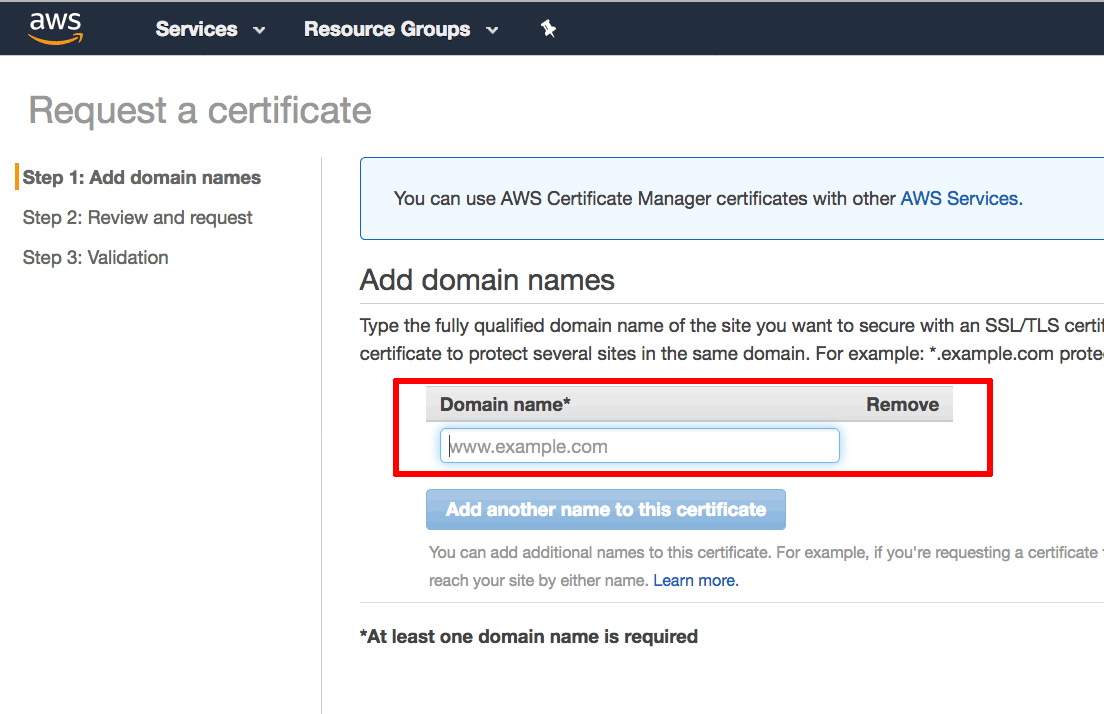
Within the AWS Certificate Manager, on the “Request a certificate” page, enter your domain name. Click “Review and request” to review and confirm the request.
NOTE: When requesting the certificate, specify both the DOMAIN and www.DOMAIN forms of the domain name to ensure that the certificate is valid for both scenarios.
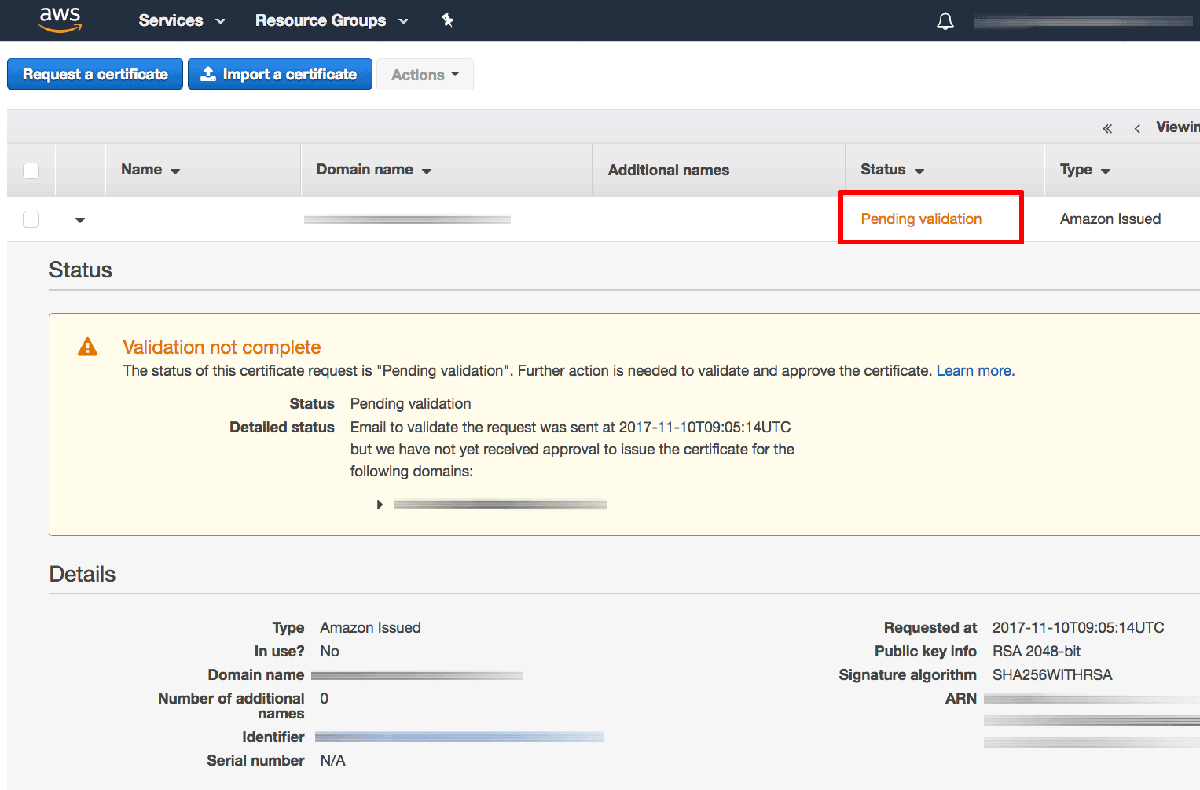
An email will now be sent to the registered owner of the domain with instructions to confirm the certificate request by validating the domain. The domain will appear in the AWS Certificate Manager with status set to “Pending validation”.
TIP: Learn more about the AWS Certificate Manager domain validation process.
Once the domain has been validated, the certificate will be issued and will appear in the AWS Certificate Manager with status set to “Issued”.
-
Back on the “Configure Security Settings” page for the load balancer, the newly-issued certificate should now appear in the list of available certificates. Select it and click the “Next: Configure Security Group” button to proceed.
-
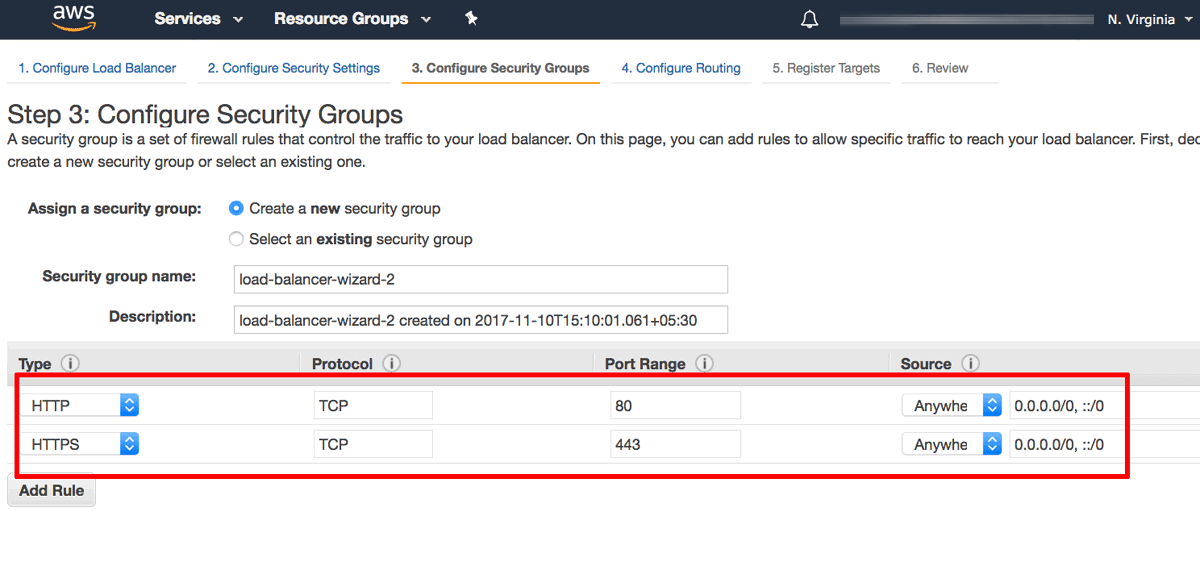
On the “Configure Security Group” page:
-
Select the option to “Create a new security group”.
-
Add a security rule to allow inbound traffic on port 80 (the HTTP port) with source “Anywhere”.
-
Add a second security rule to allow inbound traffic on port 443 (the HTTPS port) with source “Anywhere”.
-
Click the “Next: Configure Routing” button to proceed.
-
-
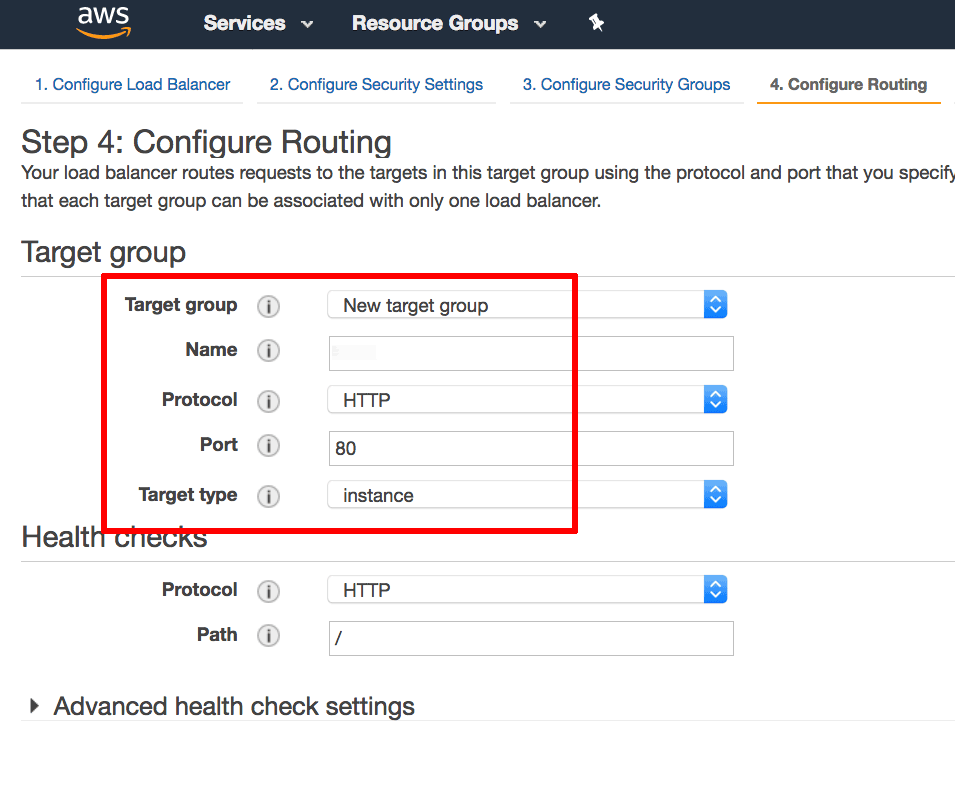
On the “Configure Routing” page:
-
In the “Target group” section, create a new target group and assign it a name. Ensure that the protocol is set to “HTTP”, the port to “80” and the target type to “instance”. With this configuration, traffic between the load balancer and the instance will be transmitted using HTTP, even for HTTPS requests made by the client to the load balancer.
-
In the “Health checks” section, define the protocol as “HTTP” and the path to “/”.
-
Click the “Next: Register Targets” button to proceed.
-
-
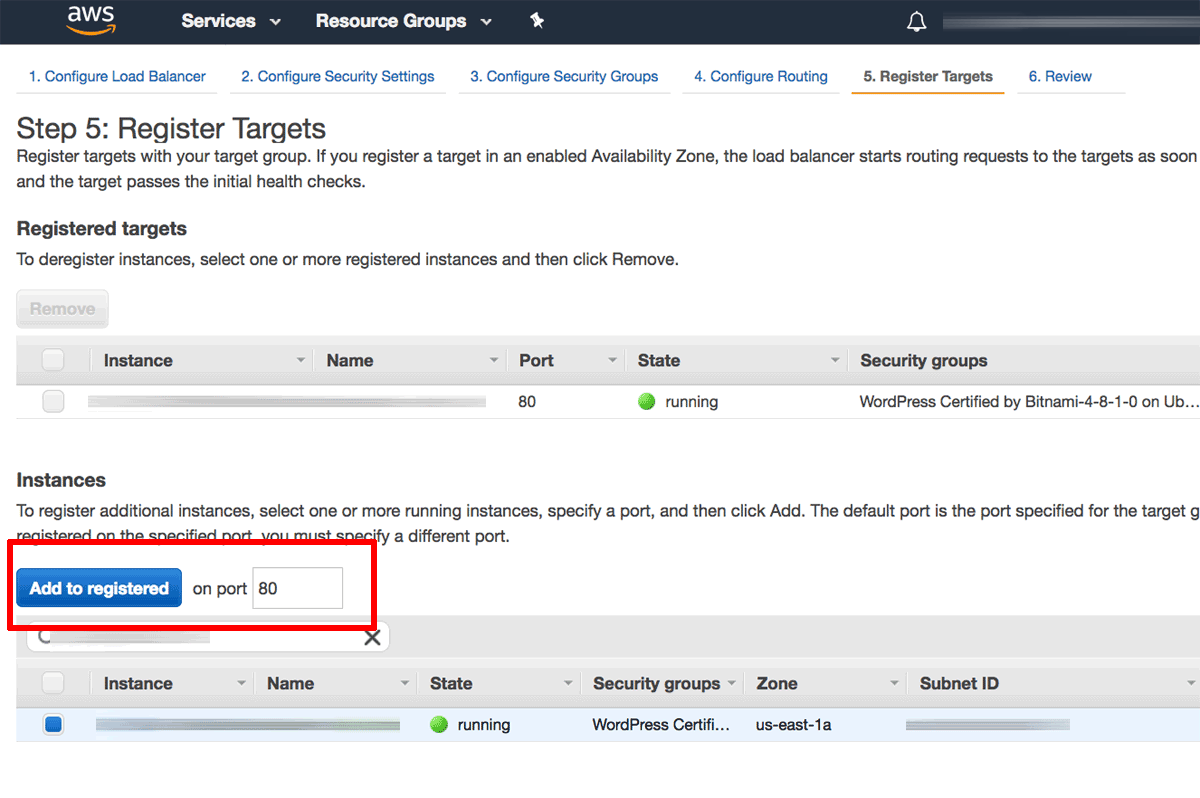
On the “Register Targets” page, use the instance ID obtained in Step 1 to identify and select the Bitnami application instance. Click the “Add to registered” button to move the instance into the list of registered targets. Click the “Next: Review” button to proceed.
-
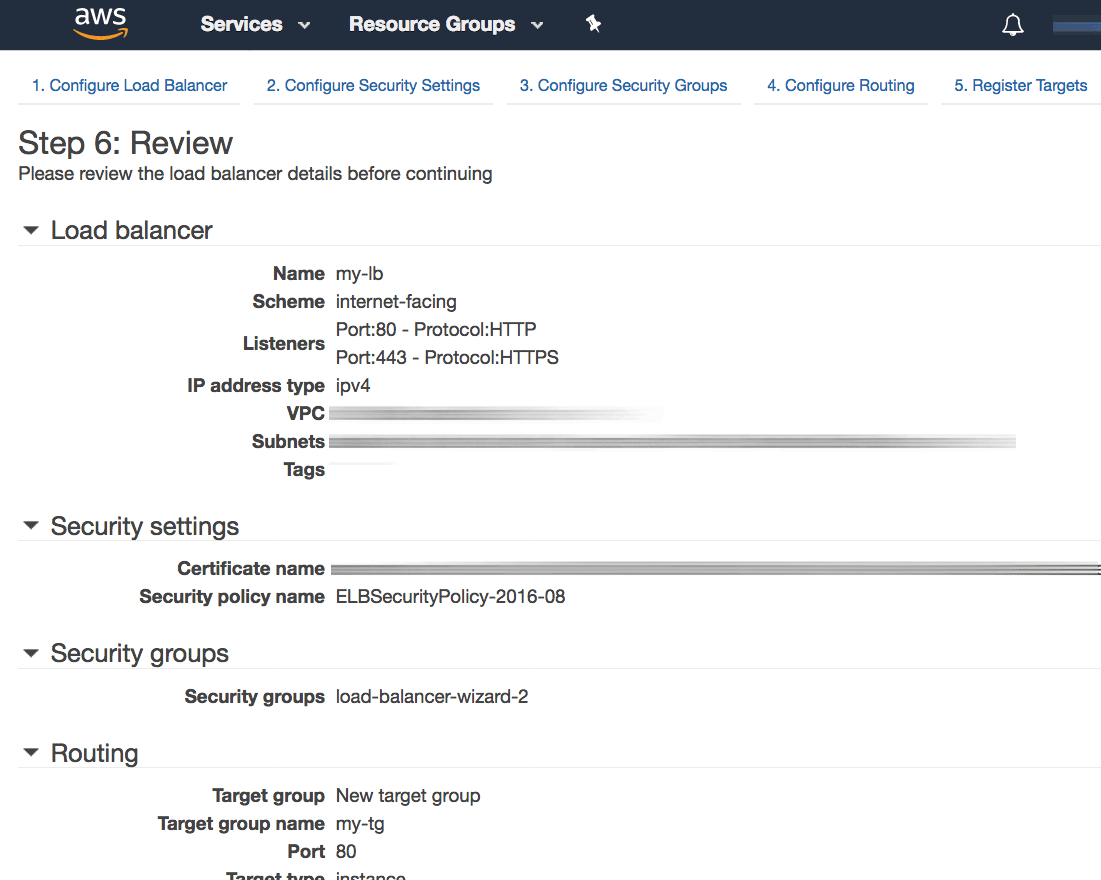
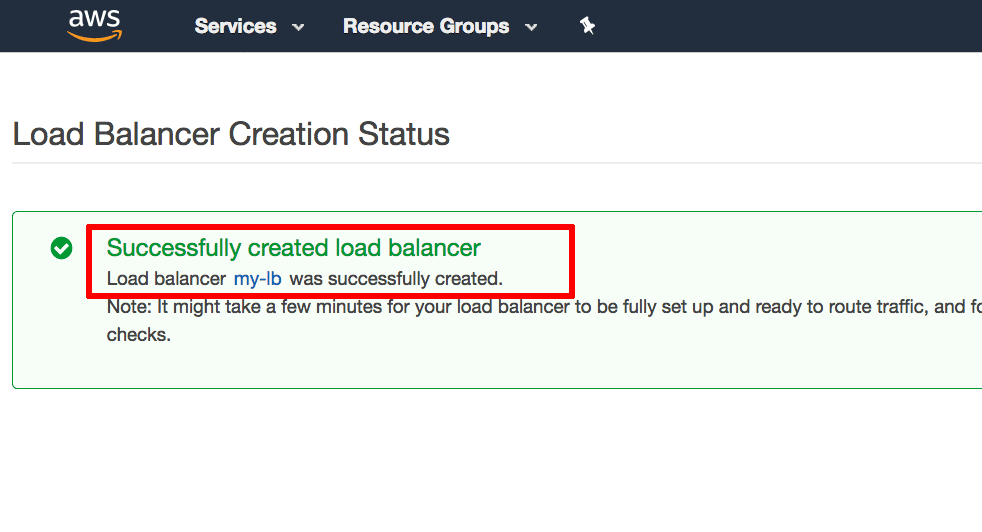
On the “Review” page, review the details of the configured load balancer. Click “Create” to confirm the configuration and deploy the load balancer.
The load balancer will now be created and deployed.
Step 3: Point your domain name to the load balancer’s IP address
Once the deployment is complete, perform the following steps:
-
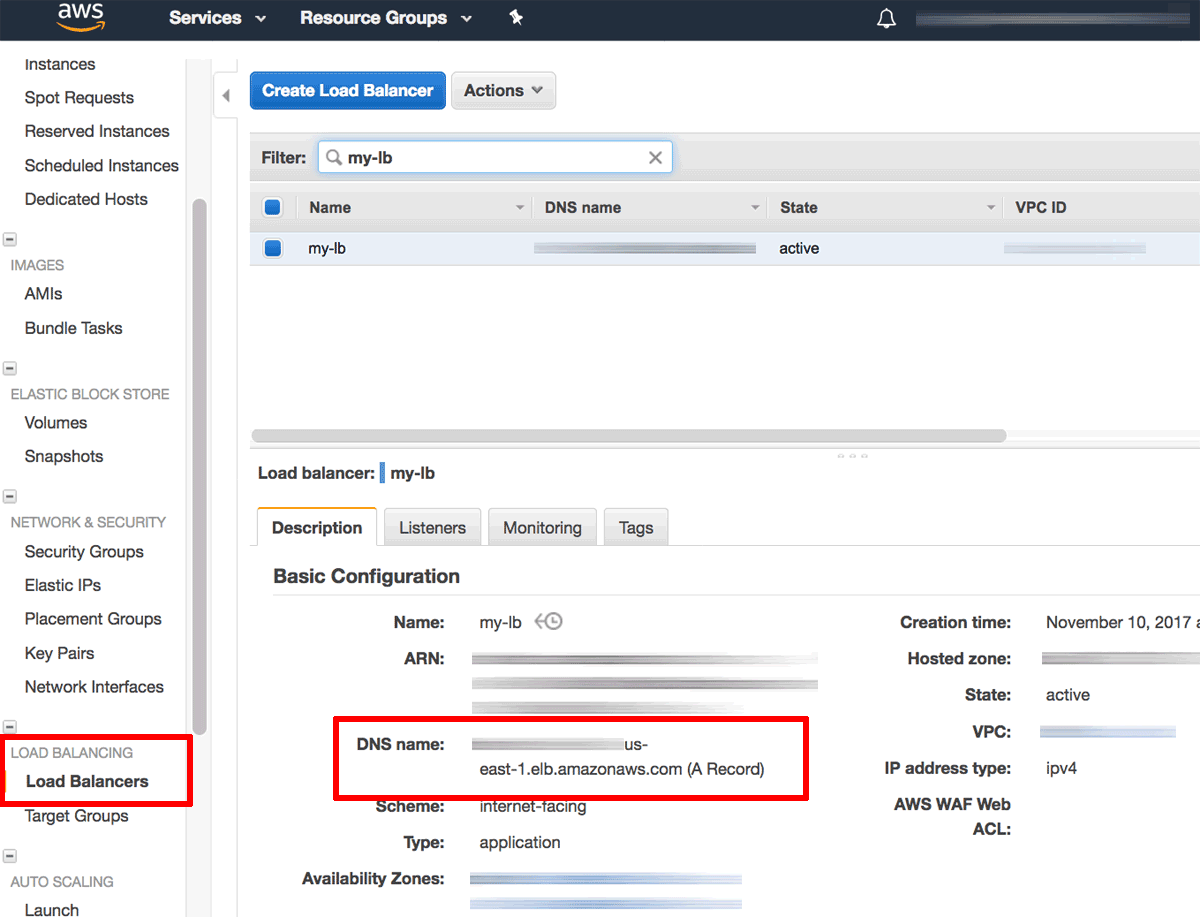
Visit the EC2 Dashboard and note the DNS name for the configured load balancer.
-
Update your domain’s DNS settings by adding an A record that points to the public DNS name of the load balancer. To do this, you will usually need to log in to your domain name provider’s management console and make the necessary changes.
NOTE: Use the DNS name (and not the IP address) of the Elastic Load Balancer in the A record, because Elastic Load Balancer IP addresses are dynamic and can change without warning.
NOTE: Once you make the necessary changes, it can take up to 48 hours for the change to propagate across other DNS servers.
Step 4: Modify the Web server configuration on the Bitnami application instance
The next step is to update the Apache server configuration on the Bitnami application instance to correctly handle SSL requests from the load balancer. To do this:
-
Modify the /opt/bitnami/apps/APPNAME/conf/httpd-prefix.conf and add the following line at the top of the file. This line ensures correct operation of the HTTP connection between the load balancer and the instance, even for load-balanced HTTPS requests.
SetEnvIf x-forwarded-proto https HTTPS=on
In some cases, it is also necessary to modify the Bitnami application configuration to automatically redirect all HTTP traffic to the HTTPS port. The procedure to do this varies per application: some applications may require you to manually edit a configuration file, others may provide an administration interface, and still others may not require any specific changes.
As an example, if you are using WordPress, you would need to edit the /opt/bitnami/apps/wordpress/htdocs/wp-config.php file and add the lines below before the WP_HOME and WP_SITEURL definitions:
if (strpos($_SERVER['HTTP_X_FORWARDED_PROTO'], 'https') !== false)
$_SERVER['HTTPS']='on';
Step 5: Force HTTPS
-
Redirect all traffic to HTTPS by adding the following to /opt/bitnami/apache/conf/bitnami/bitnami.conf
<VirtualHost *:80> ... RewriteEngine On RewriteCond %{HTTP:X-Forwarded-Proto} !https RewriteRule ^.*$ https://%{SERVER_NAME}%{REQUEST_URI} ... -
Restart the server:
$ sudo /opt/bitnami/ctlscript.sh restart apache
Step 6: Test the load balancer
Verify that the changes to your domain name record have propagated by using the Global DNS Propagation Checker and entering your domain name into the search field. After confirming that the domain name now points to the public IP address of the load balancer, you can test it as follows (replace the DOMAIN placeholder with the correct domain name):
-
Browsing to http://DOMAIN should result in the load balancer displaying the insecure welcome page of the Bitnami application.
-
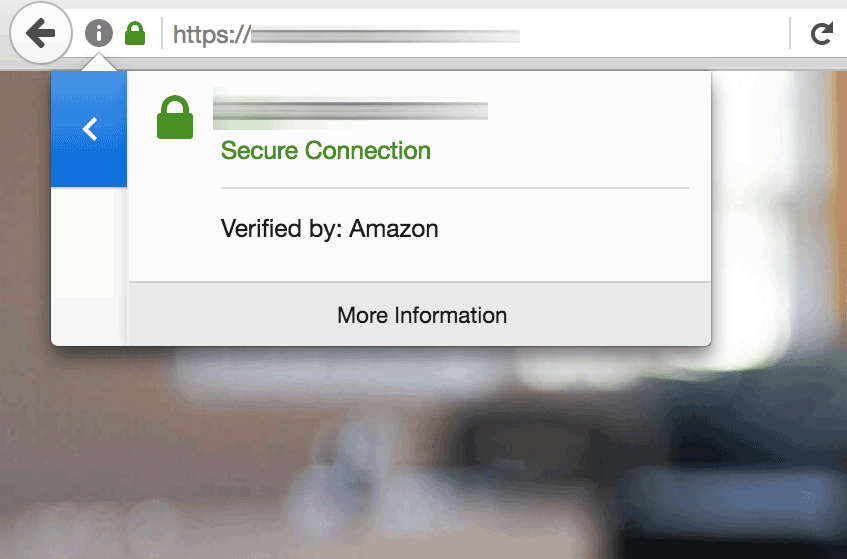
Browsing to https://DOMAIN should result in the load balancer displaying the secure welcome page of the Bitnami application. Clicking the padlock icon in the browser address bar should display the details of the domain and SSL certificate.
In both cases, the request to the HTTP or HTTPS port of the load balancer is internally transferred to, and satisfied by, the Bitnami application instance.
Your Elastic Load Balancer has now been configured with an SSL certificate for your Bitnami application running on AWS.
NOTE: If the Elastic Load Balancer is failing health checks, try using the domain name instead of the IP address for the health check.
Useful links
To learn more about the topics discussed in this guide, consider visiting the following links:
Check out the following tutorial if you want to learn more about setting up SSL using elastic load balancing: